Streamline Your DevOps Workflow with Ansible: Ad-hoc Commands, Playbooks, and Roles
A Comprehensive Guide for Automating Configuration Management Using Ansible.
Introduction:
Configuration management is a critical process in IT operations that ensures consistency and predictability of software and infrastructure deployments. Using tools and techniques allows IT teams to manage and maintain the configuration of servers, networking equipment, and other infrastructure components. Ansible is a popular open-source configuration management tool that allows you to automate the deployment and configuration of infrastructure and software in a fast, efficient, and scalable way. In this blog, we will explore the basics of configuration management using Ansible. We will cover using Ansible to automate tasks such as software installation and configuration, managing infrastructure components, and creating playbooks and roles. Whether you are new to configuration management or an experienced IT professional, join us as we dive into the exciting world of configuration management using Ansible.
Why Ansible
Before the advent of tools like Ansible, server configuration management was often done manually, or through custom scripts that had to be written and maintained for each individual platform or operating system. This approach was time-consuming, error-prone, and difficult to scale.
One of the biggest challenges in managing servers was the differences in command syntax and behavior across different platforms and operating systems. For example, a command that worked on Linux may not work on Windows, or vice versa. This meant that IT teams had to create and maintain different scripts for each platform, leading to duplication of effort and increased complexity.
Tools like Ansible have helped to address these challenges by providing a unified and standardized way of managing servers and infrastructure across multiple platforms and operating systems. With Ansible, IT teams can use a single set of playbooks and roles to manage servers running different operating systems, without having to worry about the underlying differences in command syntax or behavior. This makes it easier to automate and scale server configuration management, and helps to reduce the risk of errors and inconsistencies.
Following are some key points why Ansible is widely used 👇:
It is a push mechanism model
uses an agent-less model (no master-slave architecture)
just put the names of EC2 instances and put this file in the inventory file
scalability is much high
dynamic inventory uses automatic detection of scalability
support for Windows (Win RM) and Linux (ssh)
simple (YAML manifest)
user can write his own modules in Python and publish them using ansible-galaxy
BUT:
With windows, it's not very smooth
debugging is not easy
performance issues
Setting up Ansible on EC2
Create an EC2 instance and SSH to it
run the following command to update packages that are currently present in the instance
sudo apt updateRun the following command to install Ansible on the EC2 instance:
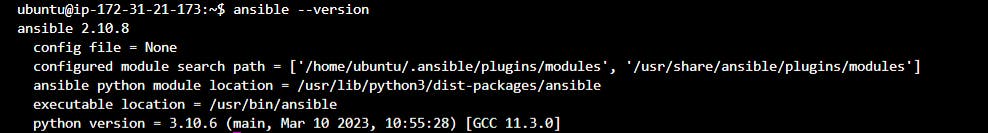
sudo apt install ansiblecheck if Ansible is correctly installed or not using the following command
ansible --versionOutput:
Configure Target Server using Ansible
- Create another EC2 instance which will be our target server.
Prerequisite:
Newly created or target servers should have password-less authentication
To generate password-less authentication on the target server 👇:
Run the following command to generate a private and public key
ssh-keygenIt will create a .ssh folder in the user's home/ubuntu directory. In .ssh there is
id_rsawhich is the private key andid_rsa.pubis the public key. Copy the public key fromid_rsa.pub
log in to the target server and open
authorized_keysand pestid_rsa.pubpreviously copied.Now try doing ssh to target servers' IP addresses and notice this time u won't be asked for any password because we have added the public key to the
authorized_keysof the target server.After checking that you are able to shh without a password use
exitcommand to exit from the target server to the original Ansible server and notice a change in IP addresses.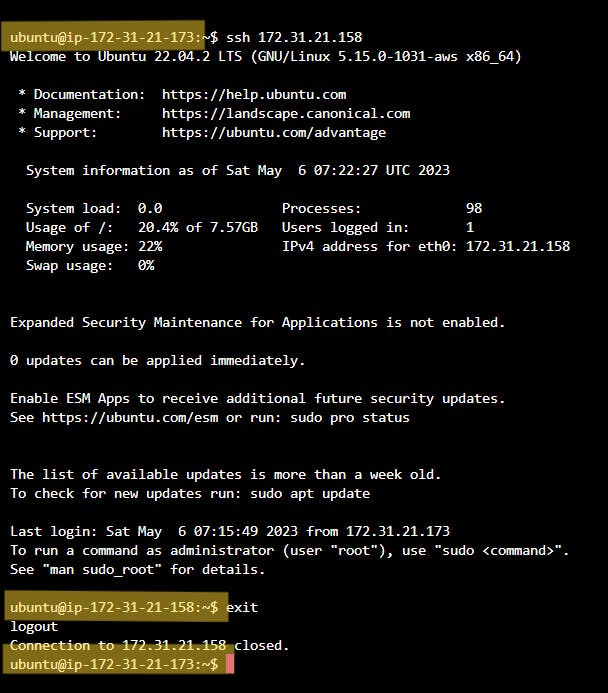
Ansible ad-hoc commands
Just like we do not have to create bash scripts always to run simple bash commands like ls or cd similarly, we don't have to write a playbook always to run Ansible commands we can do it from CLI too. They are called ansible ad-hoc commands
*inventory file = file that stores IP addresses of target servers
create an inventory file on the ansible server and add private IP addresses of the target server to the inventory file
*by default ansible stores inventory files into
/etc/ansible/hostsbut it is not always convenient to use it from here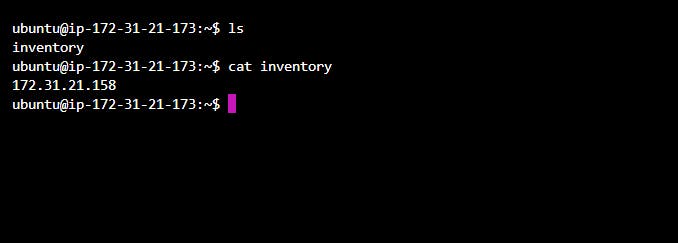
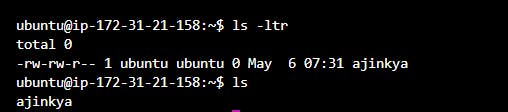
Now to demonstrate to access the target server and manage it using the ansible server we can create a file on the target server using the ansible server using the ansible command
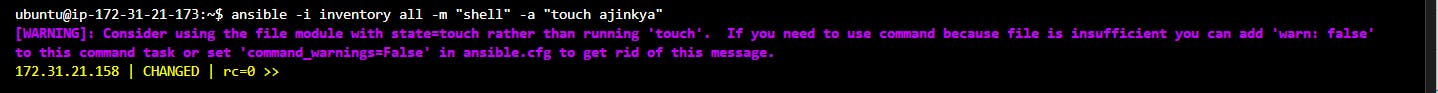
ansible -i inventory all -m "shell" -a "touch ajinkya"This command will create a file called “ajinkya” on all the target servers whose IP address is stored in inventory files.
Output
the output of the above command to create a file on the target server
output on the target server
Modules of Ansible
In the above command to create a file in the target server, we used the -m module to be a shell. There are various modules that are listed in the module documentation of Ansible. These modules are written in Python.
-m stands for modules
-a stands for what command to execute
Managing Multiple Target Servers:
If we want to deal with multiple servers we can group these servers in our inventory file by following this syntax:
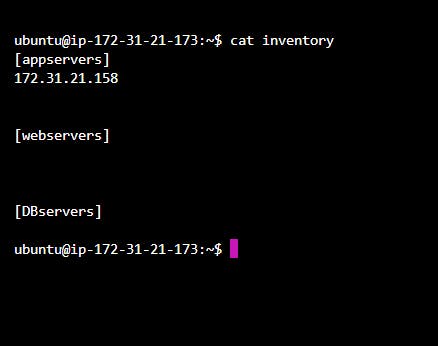
Now if we want to execute the previous command to create a file named “ajinkya” only on webservers we can modify the ad-hoc command as follows:
ansible -i inventory webservers -m "shell" -a "touch ajinkya"
Ansible Playbook:
Just like we write shell scripts to run multiple shell commands we can write an Ansible playbook to execute multiple Ansible ad-hoc commands. These playbooks are written in YAML format.
Let's say our task is to install Nginx and start the nginx we can write a playbook for it
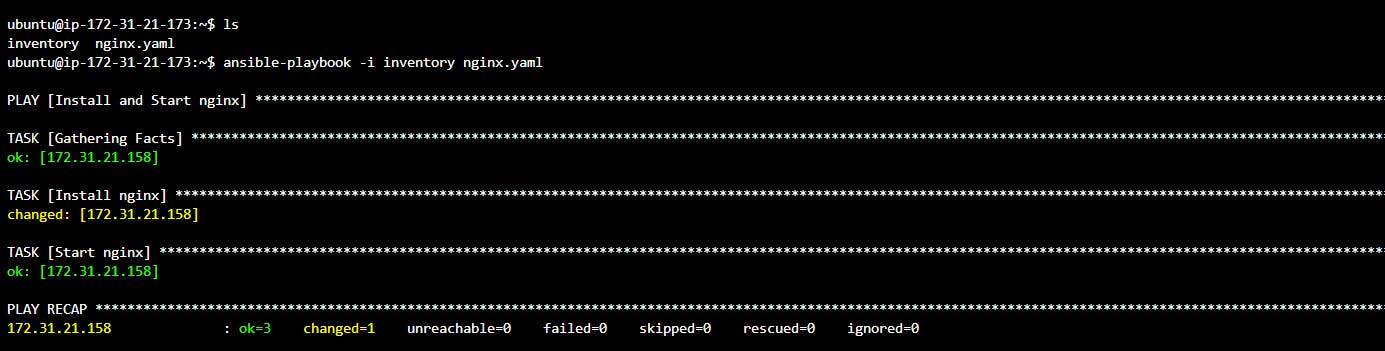
run the following command to create a playbook named nginx which is of yaml type
touch nginx.yamladd the following YAML code to this playbook
--- - name: Install and Start nginx hosts: all become: true tasks: - name: Install nginx apt: name: nginx state: present - name: Start nginx service: name: nginx state: startednow you can run this playbook using the following command
ansible-playbook -i inventory nginx.yamlOutput:
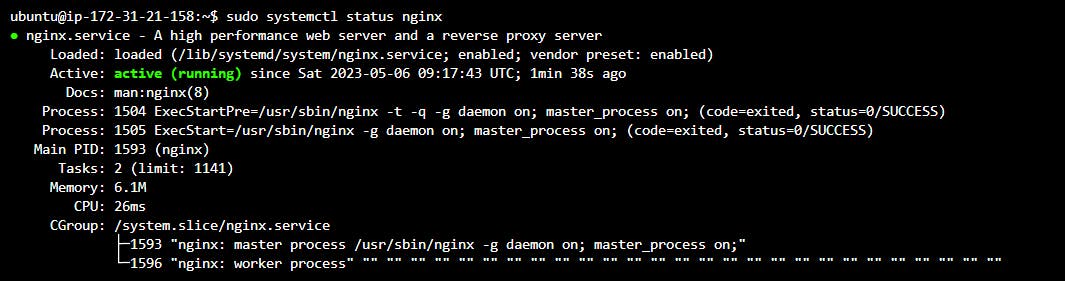
Now we can check actually installation of nginx on the target server by running the following command on the target server:
sudo systemctl ststus nginxOutput:
Ansible roles:
It is an efficient way to write complex playbooks
Let’s start understanding roles with the example:
if we want to create a role for k8s we can follow these steps:
create new directory
mkdirt k8sRoleinitialize role using the following command
ansible-galaxy role init kubernetesOutput:
this creates a folder called Kubernetes which has multiple files which help us to write our playbook effectively
now you can use this structure and run your playbook using roles
Conclusion:
In conclusion, Ansible is a versatile and powerful configuration management tool that allows IT teams to automate infrastructure and software deployments quickly and efficiently. It simplifies the management of servers and infrastructure across multiple platforms and operating systems, making it easier to automate and scale server configuration management.
This blog covered the basics of Ansible, including setting it up on EC2 and using ad-hoc commands to configure target servers. We also explored how Ansible playbooks and roles can help manage complex infrastructure and automate repetitive tasks, increasing productivity and reducing errors.
In summary, Ansible is a must-have tool for any IT professional looking to streamline configuration management processes, increase efficiency, and reduce the risk of errors and inconsistencies. Its versatility and extensibility make it a valuable addition to any modern IT infrastructure.
Reference:

